Overview
What Is Centralized Management of Cybersecurity?
Centralized management in cybersecurity involves overseeing all security processes across an organization using a single set of tools and procedures. This approach streamlines planning, implementation, monitoring, and compliance efforts, reducing miscommunication and redundant tasks. By consolidating cybersecurity operations into one system, administrators can efficiently manage security measures without navigating multiple consoles or configurations. Integration with virtualization and directory services enhances visibility and security monitoring. This unified approach ensures comprehensive protection for the entire IT infrastructure, eliminating disparities in security levels across different network components.
The Challenge
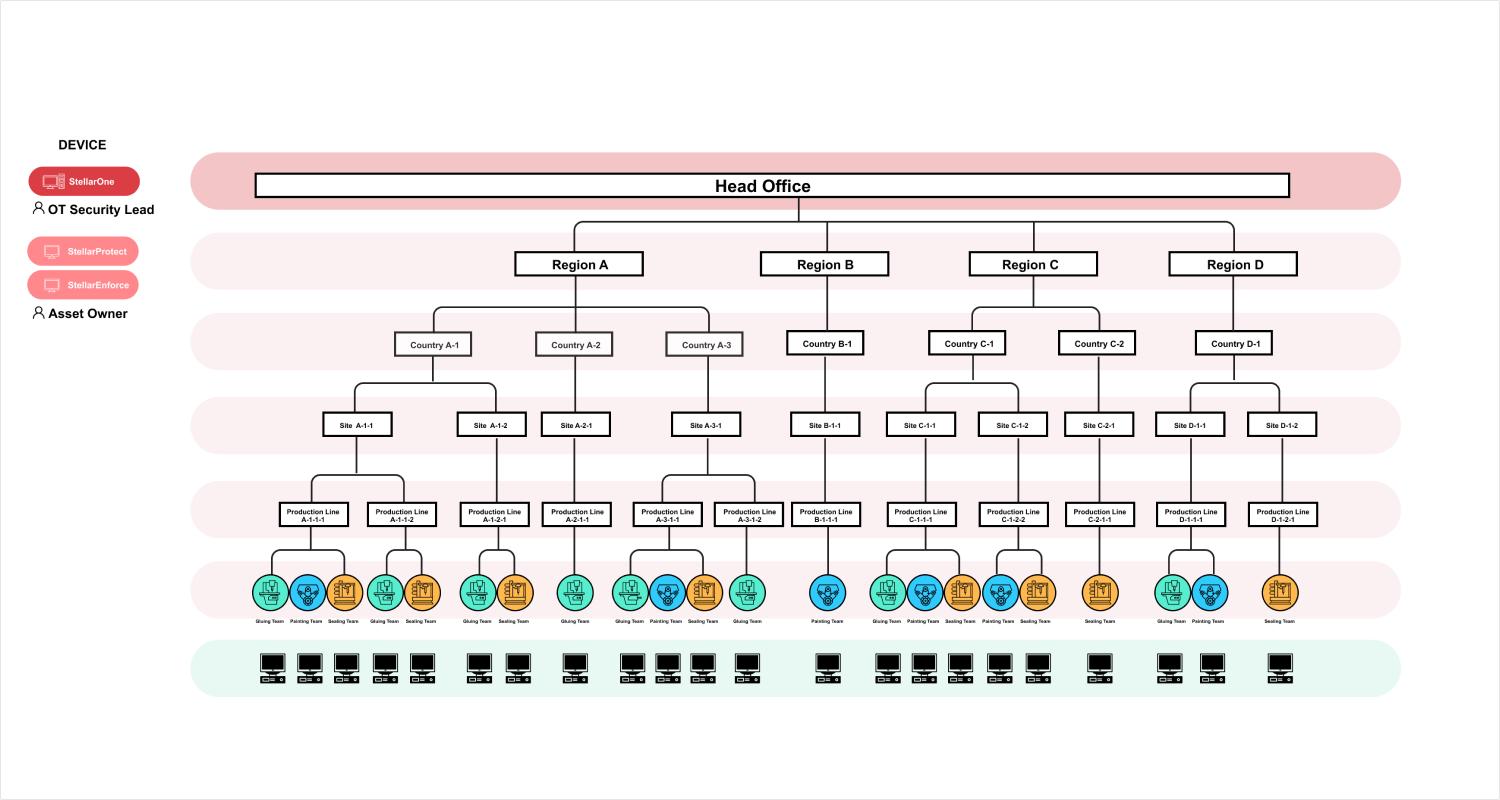
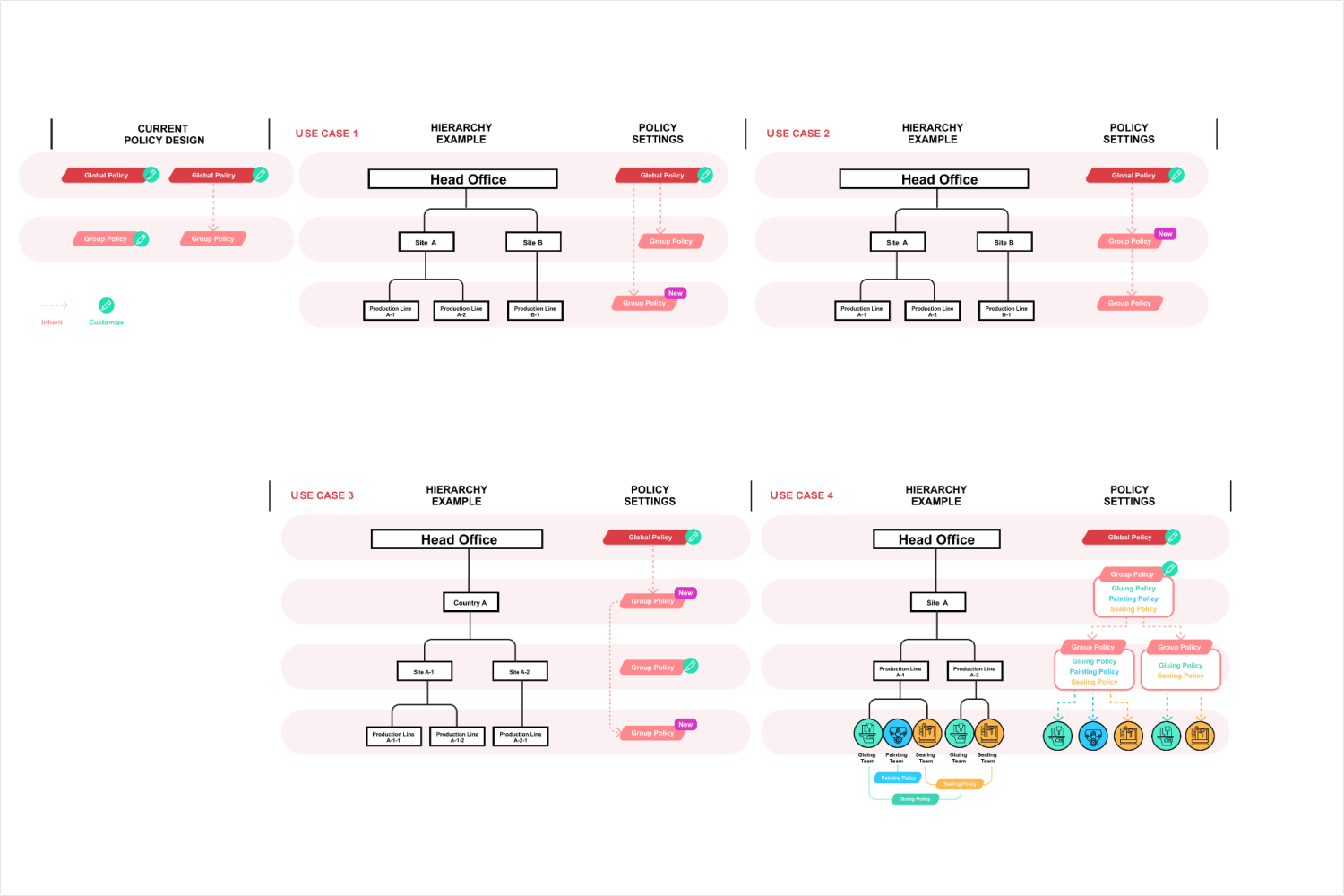
#1 Multiple Layered Management Structure
The existing system lacks a cohesive management structure, so a hierarchical management structure is essential for large organization structure. With most functions confined to a single layer within the group, managing security configurations becomes challenging and inefficient.
Implement a hierarchical structure for policy inheritance and customization
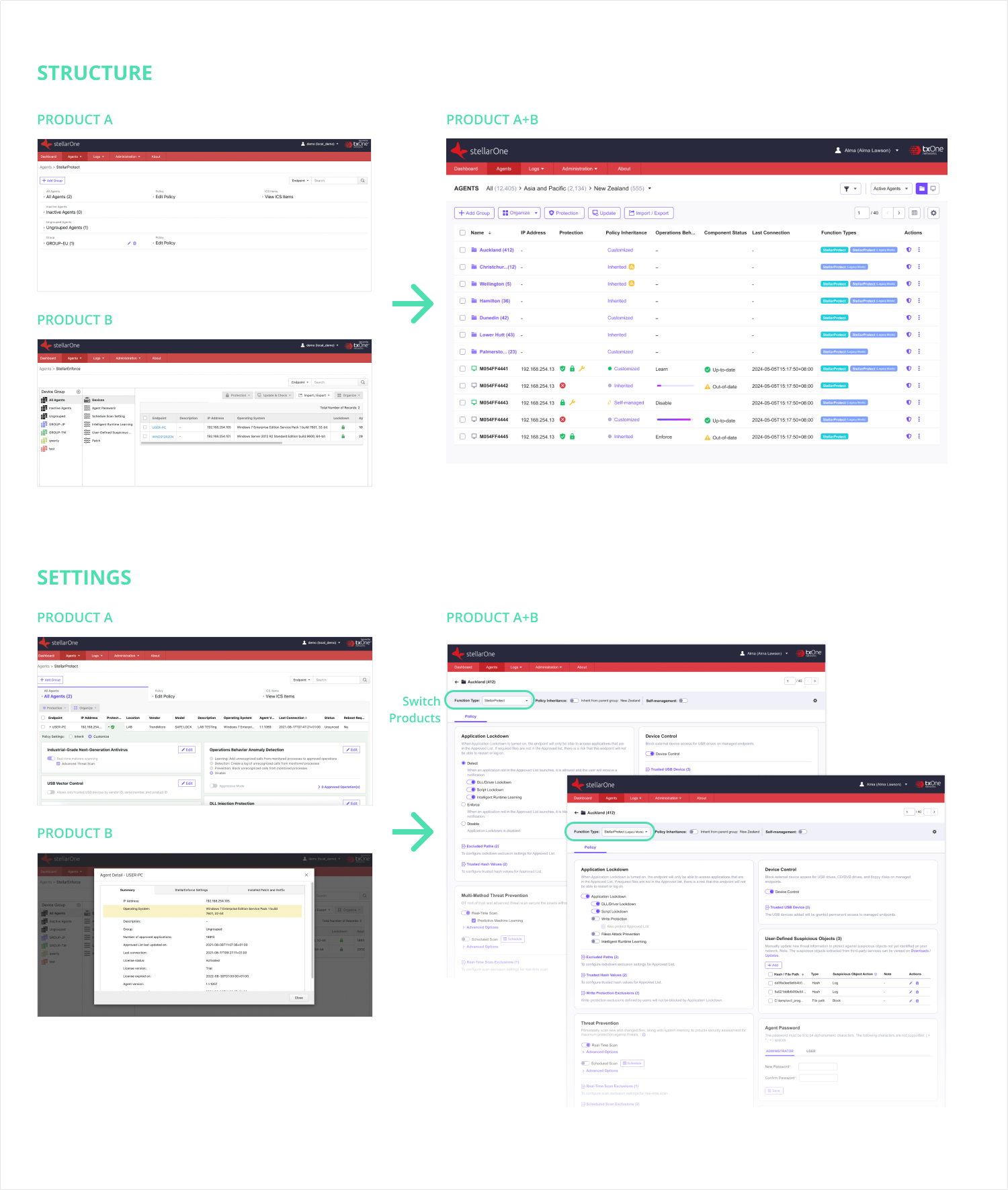
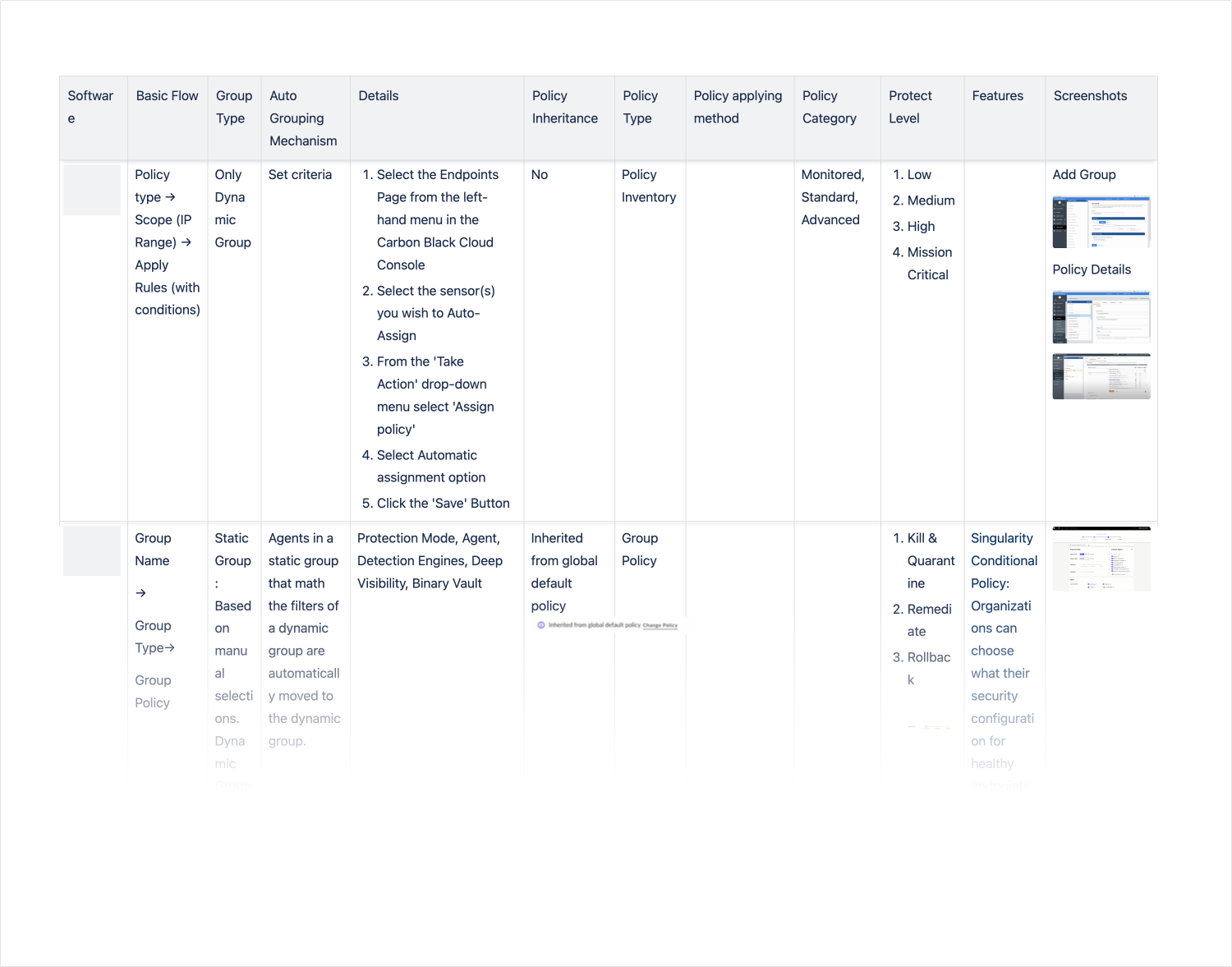
#2 Merging Two Different Product Structures and User Interfaces
Combining two products designed for different targets poses significant challenges due to differing functionalities, user interfaces, and the grouping structures. Not only are the functions distinct but the user interfaces and grouping structures also vary significantly between the two products.
Conduct a comprehensive review to align functions across both products:
Ensure flexibility in the user interface to accommodate both products:
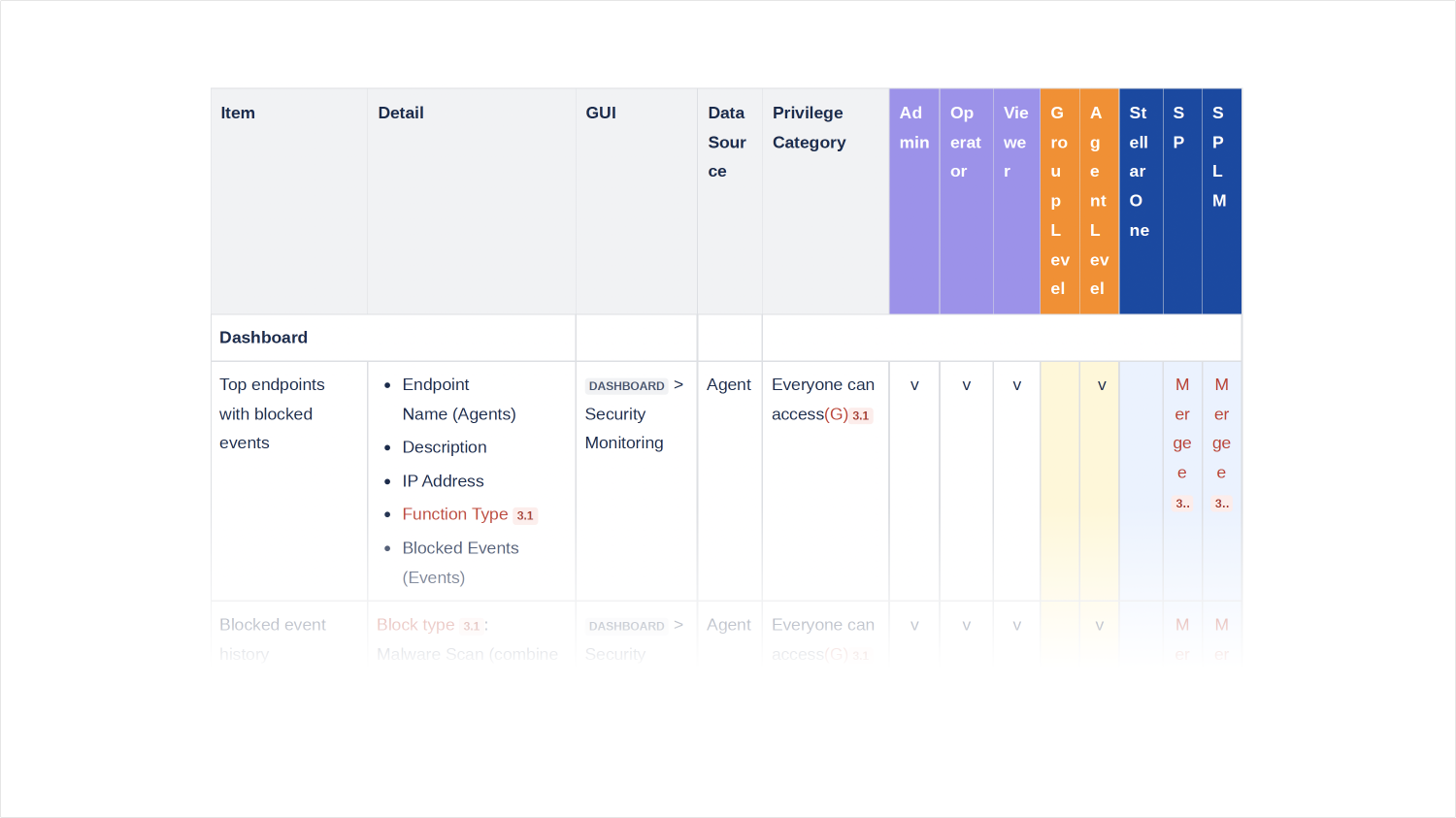
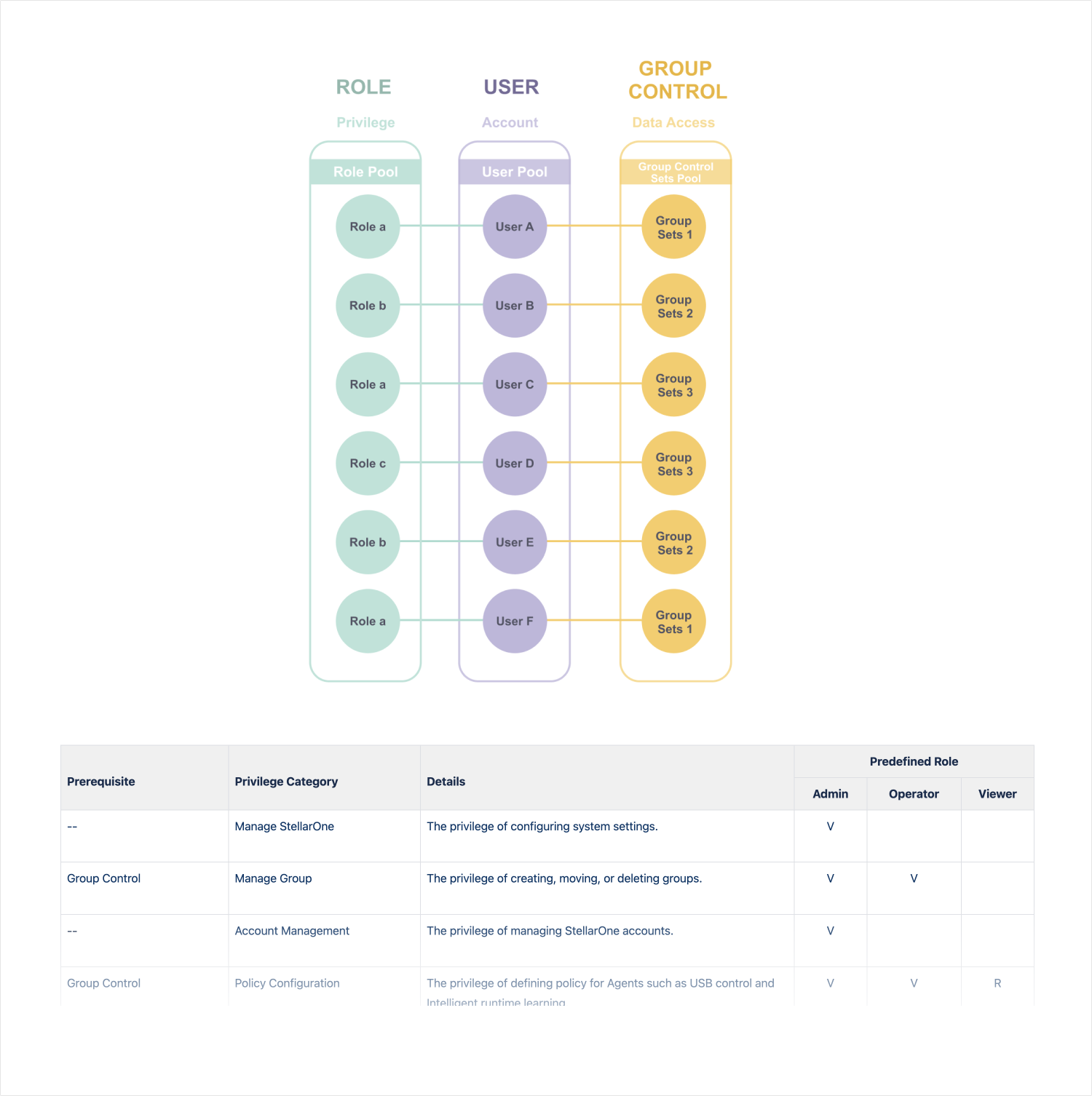
Unclear Definition for Account Roles and Customized User Access Rights
The system lacks clear definitions for account roles and customized user access rights, leading to ambiguity and potential issues. With three roles in the system, the functions assigned to each role are poorly defined. Moreover, some users require limited access restricted to specific managed groups only.
Persona
Conduct streamlined interviews with existing customers. Similarly, engage internal colleagues such as product managers, support teams, and sales representatives to glean insights about the environment and roles.
User roles within the system are categorized into three main categories:
Admin
- Admins have full power and authority over the system.
- They can access and manage all aspects of the system, including configuration, settings, and user permissions.
- Admins are responsible for overall system maintenance, security, and governance.
Operator
- Operators are individuals designated as the primary managers of their respective groups within the system.
- They have authority over their group's status, configuration, and protection settings.
- Operators are responsible for monitoring and managing the security posture of their assigned groups, ensuring compliance with policies and procedures.
Viewer
- Viewers are users who require access to the system for auditing purposes.
- They have limited permissions focused on viewing and analyzing system data and reports.
- Viewers typically conduct audits on specific issues periodically, such as annually or quarterly, to ensure compliance and identify any potential security concerns.
By dividing user roles into these three categories, the system ensures appropriate access levels and responsibilities for different user roles, facilitating efficient operation and governance.

Process
Competitive Analysis
The research scope focuses on three key areas: RABC (Role-Based Access Control), central management structure, and the design system. RABC involves implementing a system that controls access to resources based on user roles within the organization, ensuring appropriate permissions and access levels. The central management structure aims to streamline organizational processes by consolidating management protection. Also, the design system encompasses developing a cohesive framework for the organization's digital products and services, defining design principles, creating reusable components, and maintaining consistency across platforms for an improved user experience and brand identity.
User Interview and Affinity Diagram
We have developed a prototype with task-based user interview materials. Two key insights have emerged from these interviews:
Insight #1
The installation process for the two products is separated. This indicates a potential need for integrating the installation process to enhance user experience and efficiency.

Insight #2
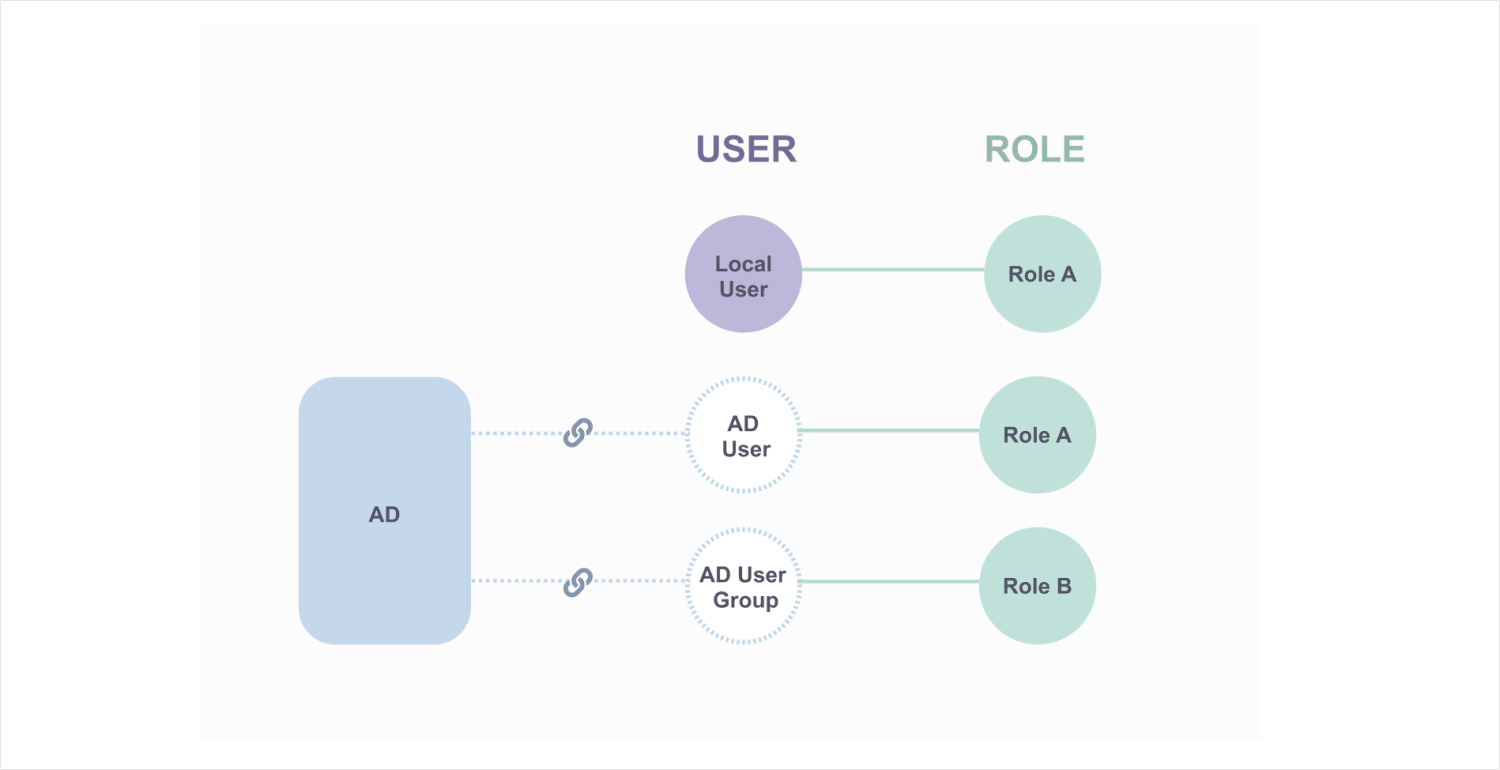
Users express the requirements of Active Directory (AD) group integration for user account management for user account management effectively.
Ideation
Information Architecture
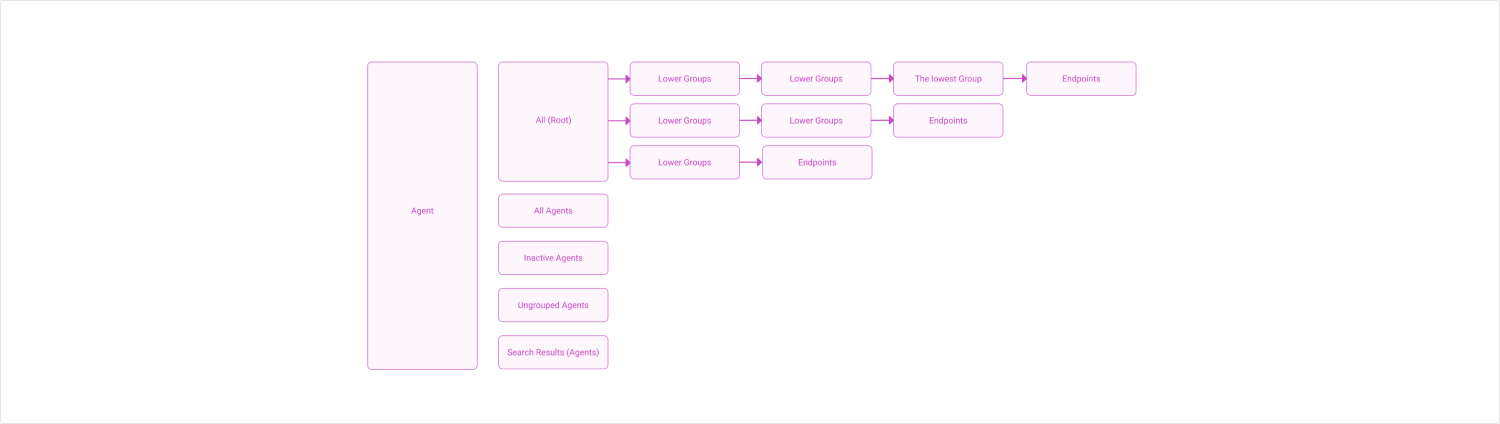
Wireframe

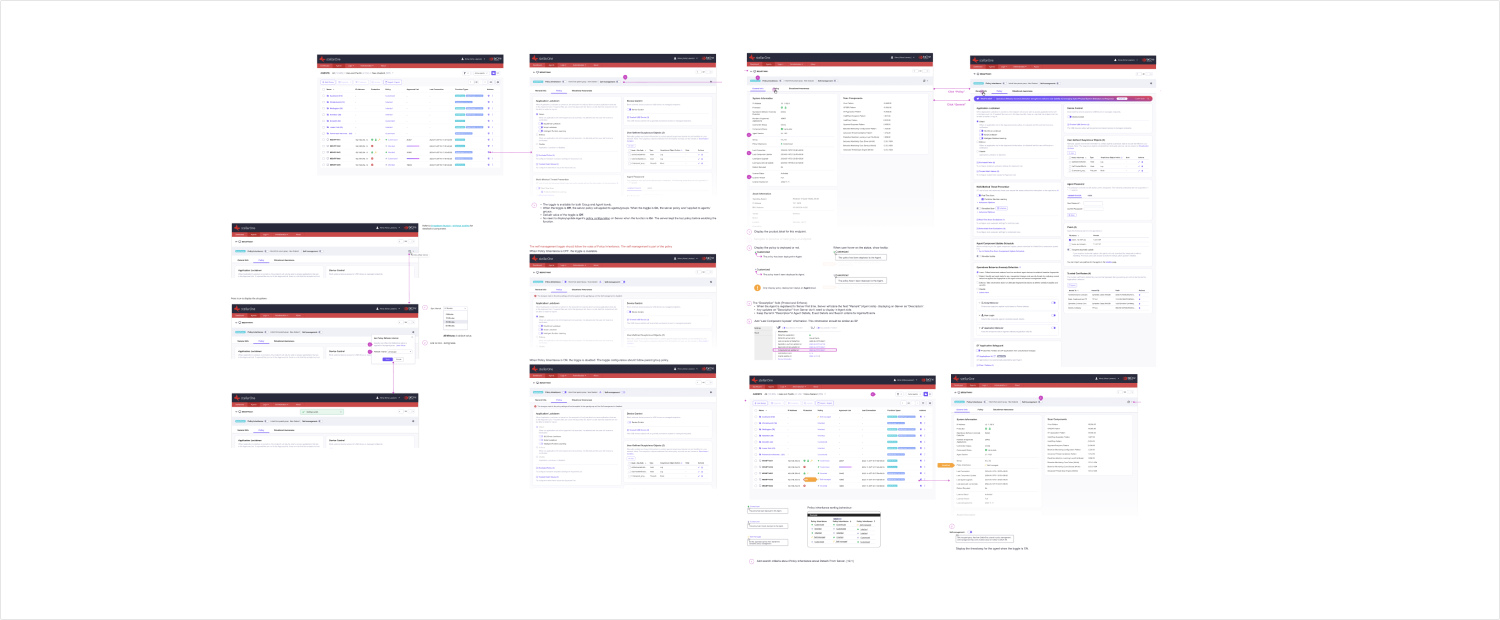
Design
UI Flow
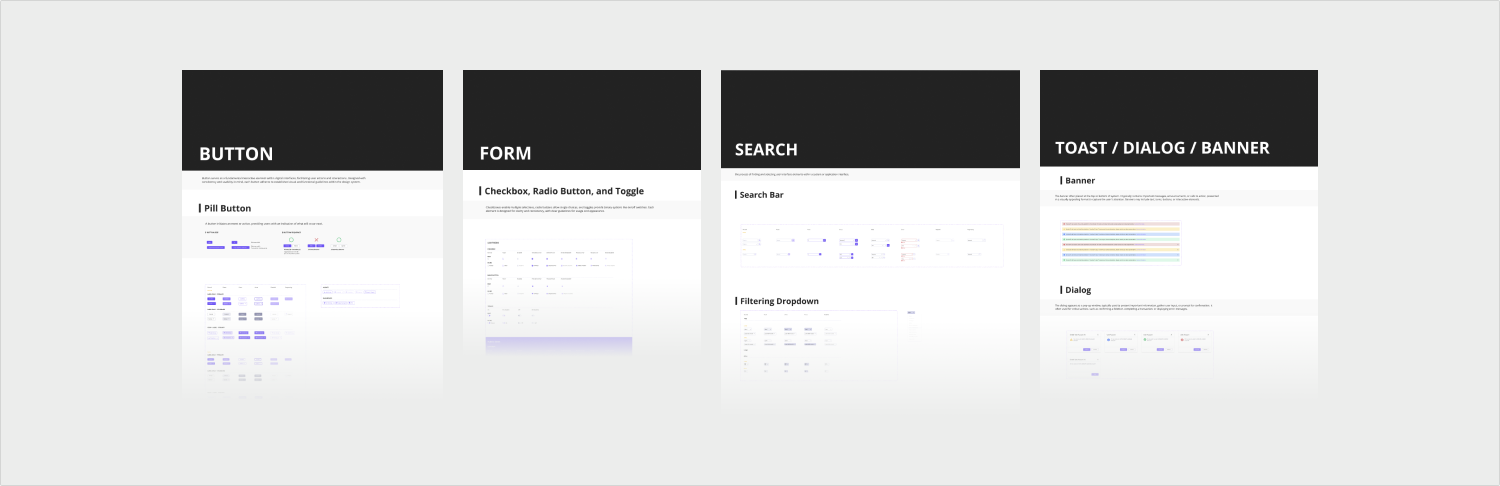
Design System
I have structured a comprehensive branding-focused design system, which comprises the following components:
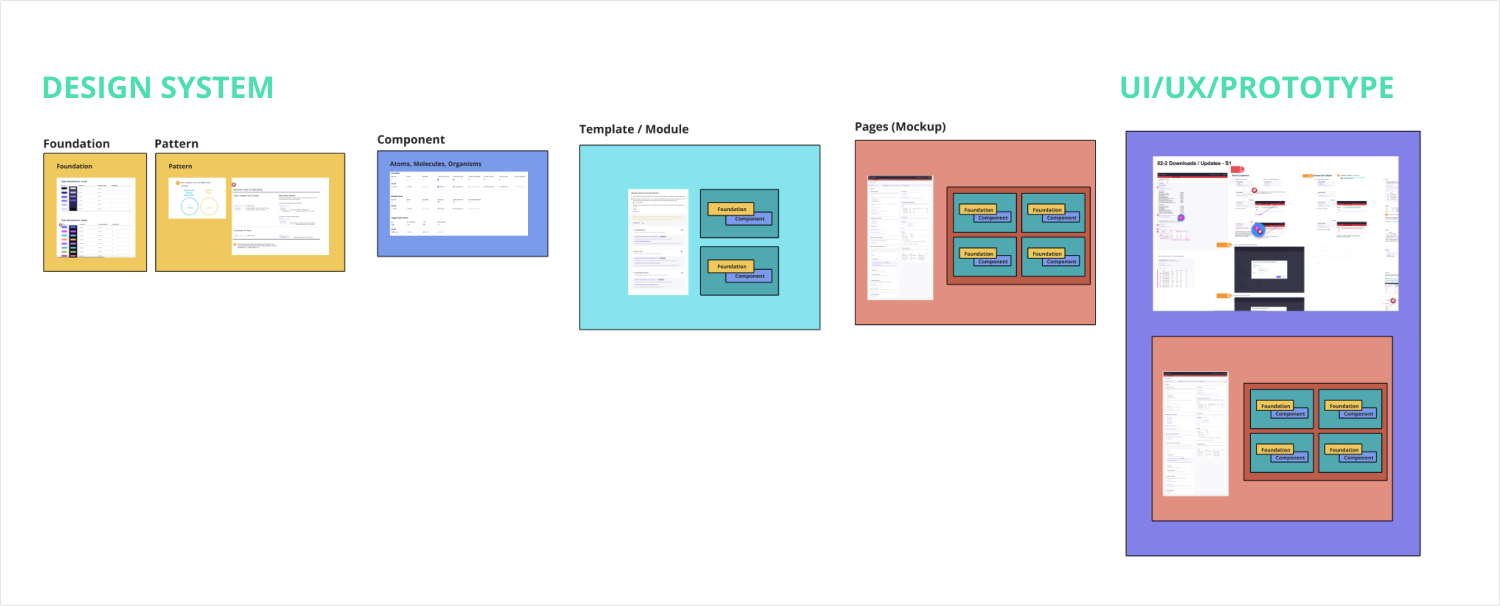
- Foundation: colors, typography, icons, illustrations, gird...
- Pattern: search, table, import/export behavior…
- Components:
- Elements: Buttons, Labels…
- Data Entry: Form, Search bar, Selector…
- Data Display: table, onboarding message, widget…
- Feedback: Banner, Toast, Loader…
- Navigation: Menu, Tab…