Project Brief
What Is CPSDR?
CPSDR stands for Cyber-Physical System Detection and Response, a groundbreaking feature set in cybersecurity. Interacting digital, analog, physical, and human components engineered for function through integrated physics and logic.
Overview
A Pioneer of the Industry
To be pioneers in our industry with a groundbreaking new feature, we introduce a cutting-edge addition to our platform. We are committed to pushing the boundaries of what is possible, leveraging the customer needs in operational industry.
The Challenge
Users lack familiarity with this innovative feature, with only a few possessing IT experience related to it. However, the experience of Operational Technology (OT) users differs significantly from that of IT Endpoint Detection and Response (EDR) users. This pioneering initiative presents unique challenges as it leads the industry forward with its innovative approach.
Process
Competitive Analysis
Finding #1
Our discovery revealed that while EDR (Endpoint Detection and Response) stands as the main solution for users of this feature, it's not perfectly suited for OT (Operational Technology) users since: Firstly, OT teams typically have fewer members involved in operating security software. Secondly, EDR's powerful response data capabilities may pose challenges in fitting into OT environments, where the operational technology system should remain unaffected.
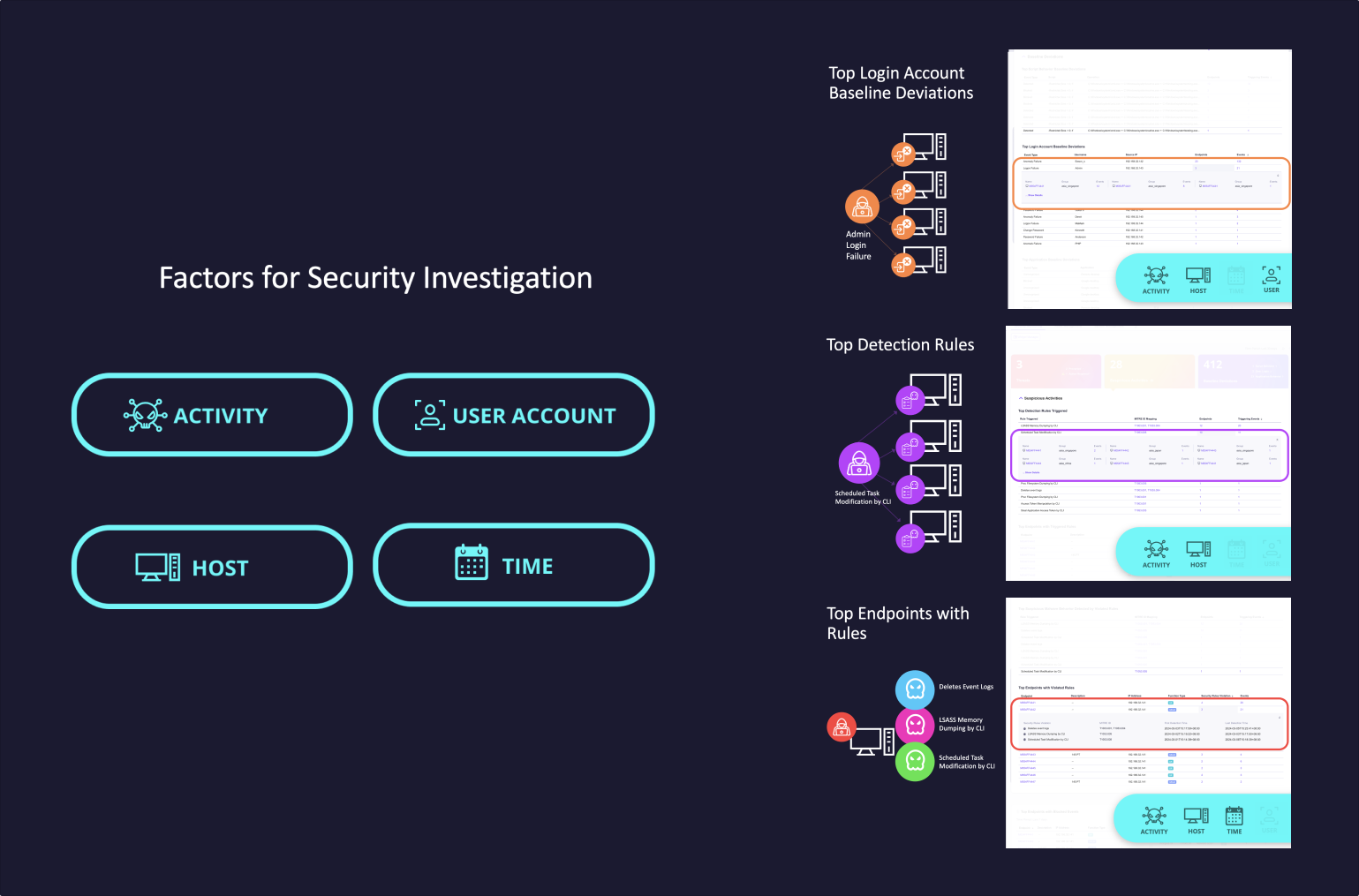
Finding #2
We identified four critical factors that facilitate user investigation into security issues: activity, host, user, time.
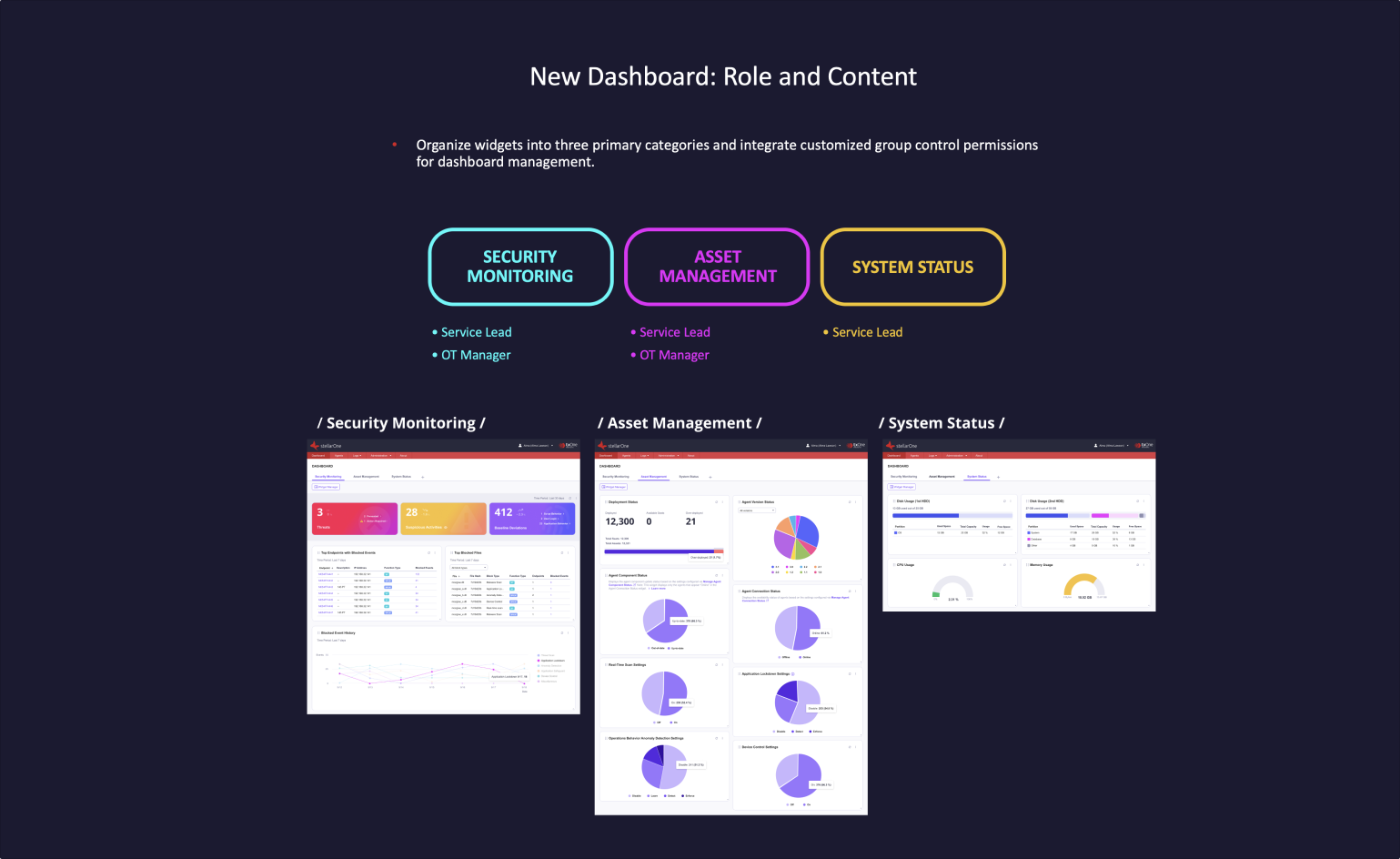
Widget Evaluation
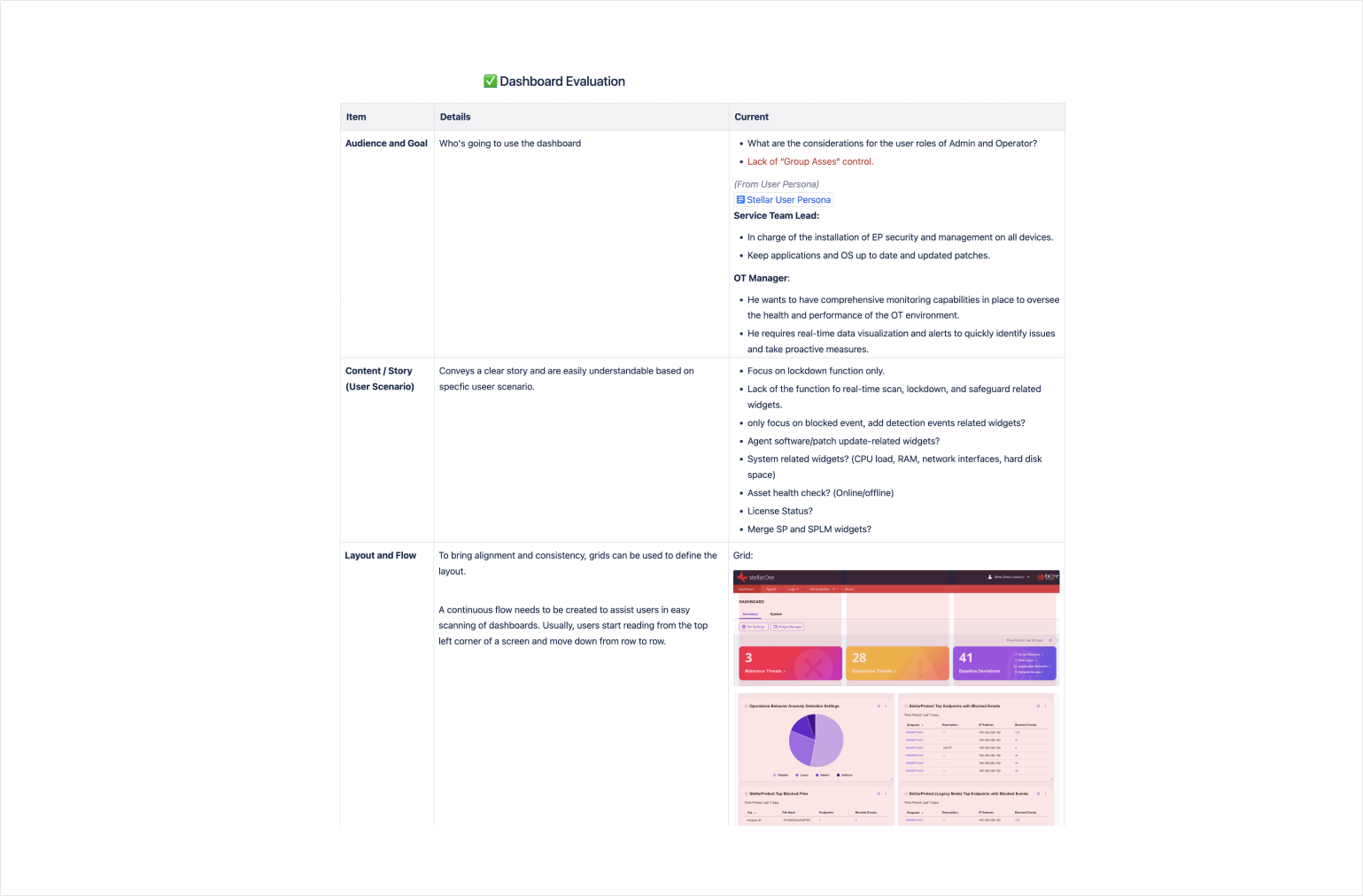
During this phase, I thoroughly assess the current dashboard's inclusivity and accessibility, ensuring it caters to diverse user needs. I examine representation, readability, and usability to identify areas for improvement and enhance the overall user experience.
Persona
To conduct interviews with internal stakeholders and existing customers to understand their dashboard needs.
Service Lead
- Responsible for installing security on all devices.
- Ensures applications and operating systems are consistently updated with the latest patches.
OT Manager
- Seeks comprehensive monitoring capabilities for overseeing the health and performance of their own team/group.
- Requires real-time data visualization and alerts to swiftly identify issues and proactively take corrective measures.
User Journey
This user journey represent the sequential stages of learning, detecting, enforcing, and receiving result alerts of this new function.
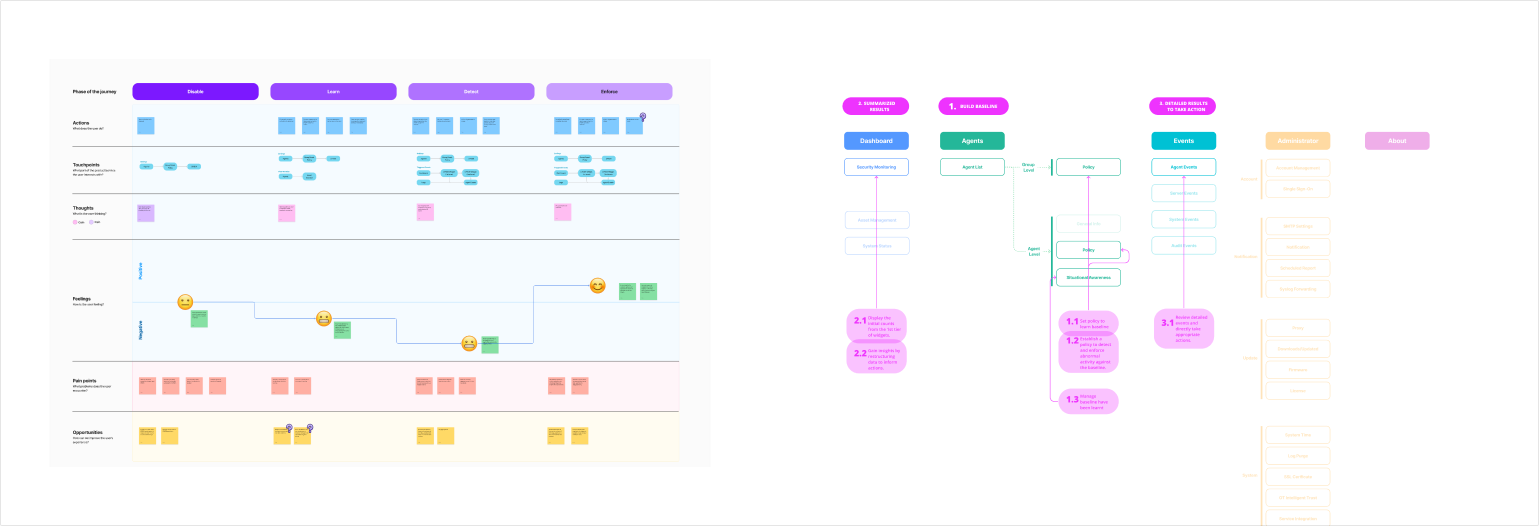
Insight #1
Importance of Onboarding experience: Since this function is entirely new in the industry, users may feel uncertain about its functionality and benefits. They may also worry about how it will affect their operations and the possibility of false alarms. To make things easier, we offer users a simple shortcut to quickly learn about the function, ensuring a smoother onboarding experience.
Insight #2
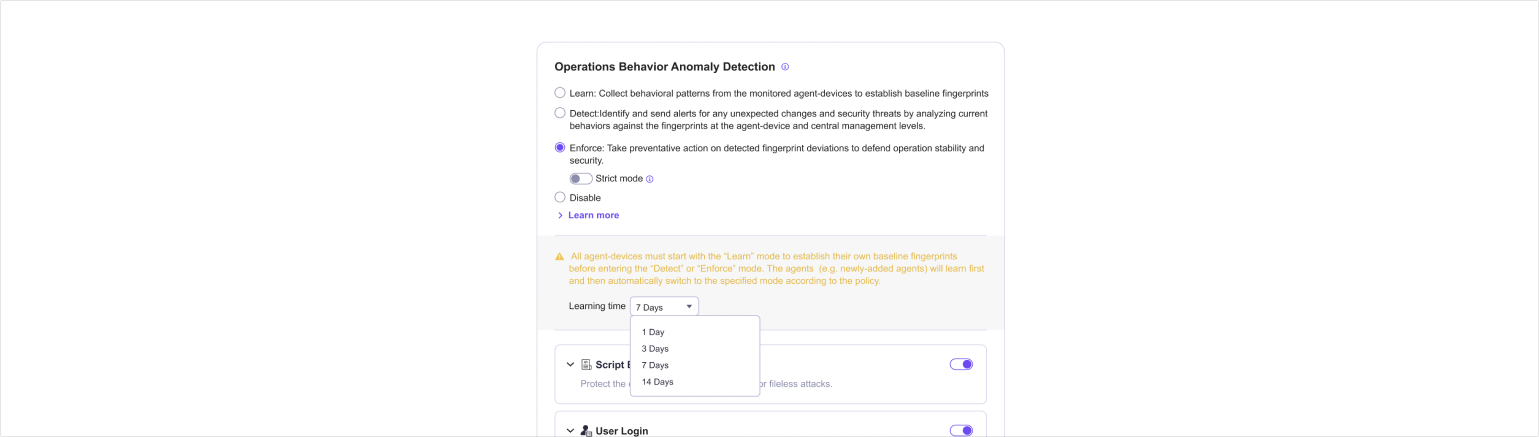
Learning Phase Challenges: Starting and completing the learning phase can be tough for users. To help, we've introduced an auto-learning system and provided users with helpful suggestions to launch their usage journey effortlessly.
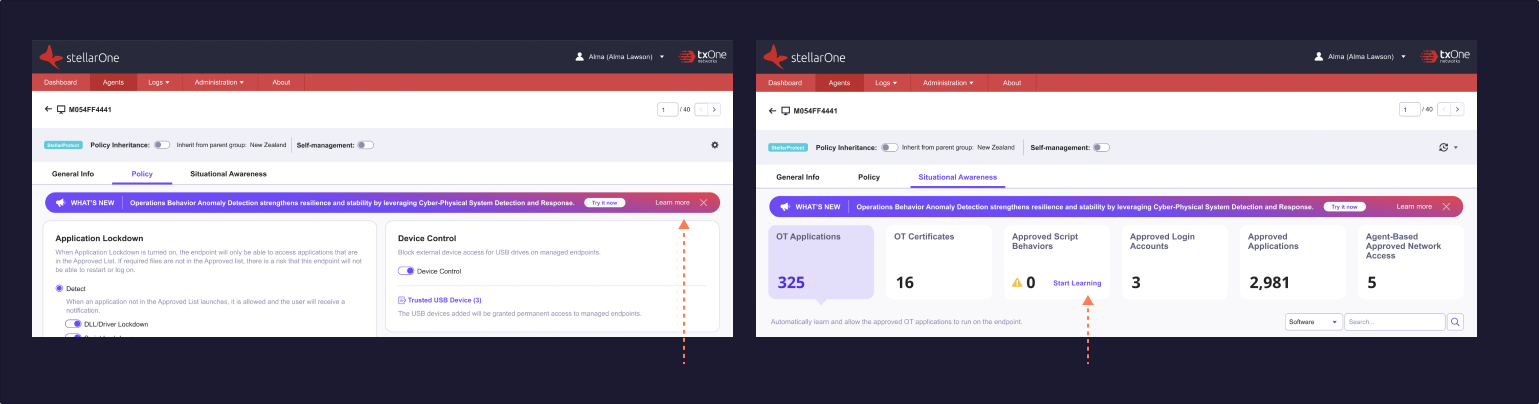
User interview and Usability Test
The interview and test encompasses internal users, external users, and analytics experts such as Gartner and Forrester.
Insight #1
In user interviews, we found users prioritize spotting suspicious activities over malicious ones. Malicious actions often prompt immediate responses, while suspicious activities may pose higher risks from advanced attackers. This insight guides us in improving our platform's ability to detect and respond to security threats, enhancing users' security management.
Insight #2
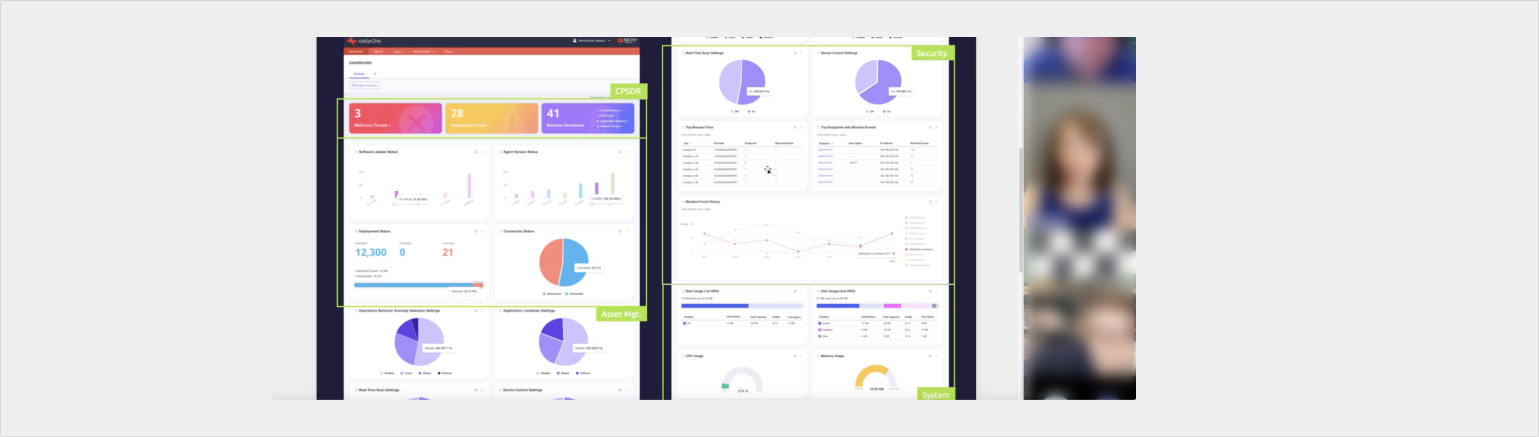
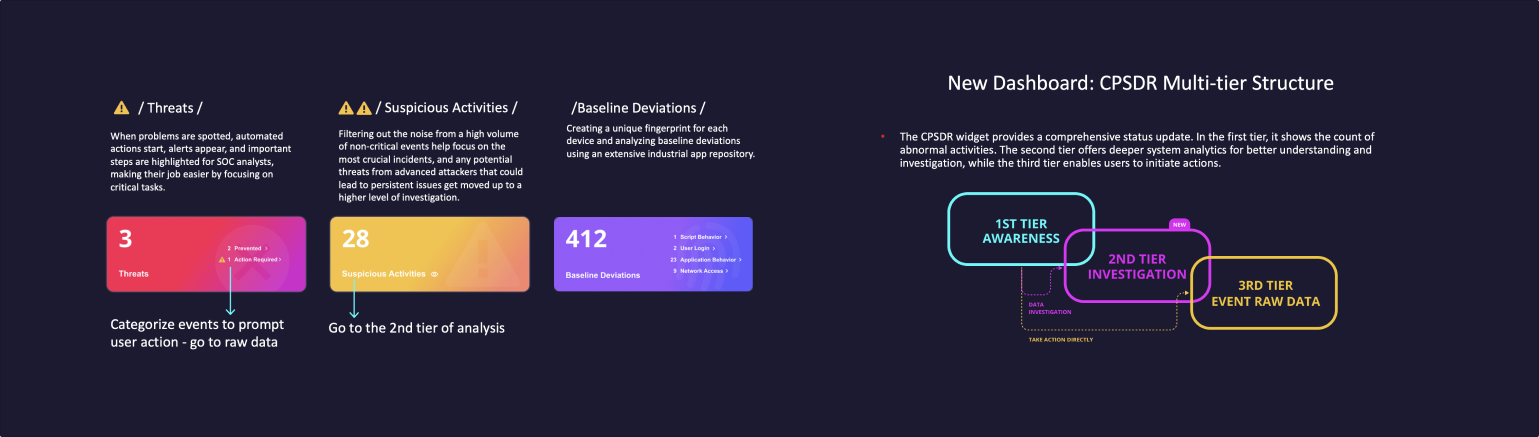
Users find it challenging to interpret the results and determine appropriate actions. To address this, we provide a comprehensive status update with a three-tier structure. The first tier displays the count of abnormal activities, providing users with a quick overview. The second tier offers deeper system analytics for better understanding and investigation. Finally, the third tier enables users to initiate actions in the raw data.
Ideation
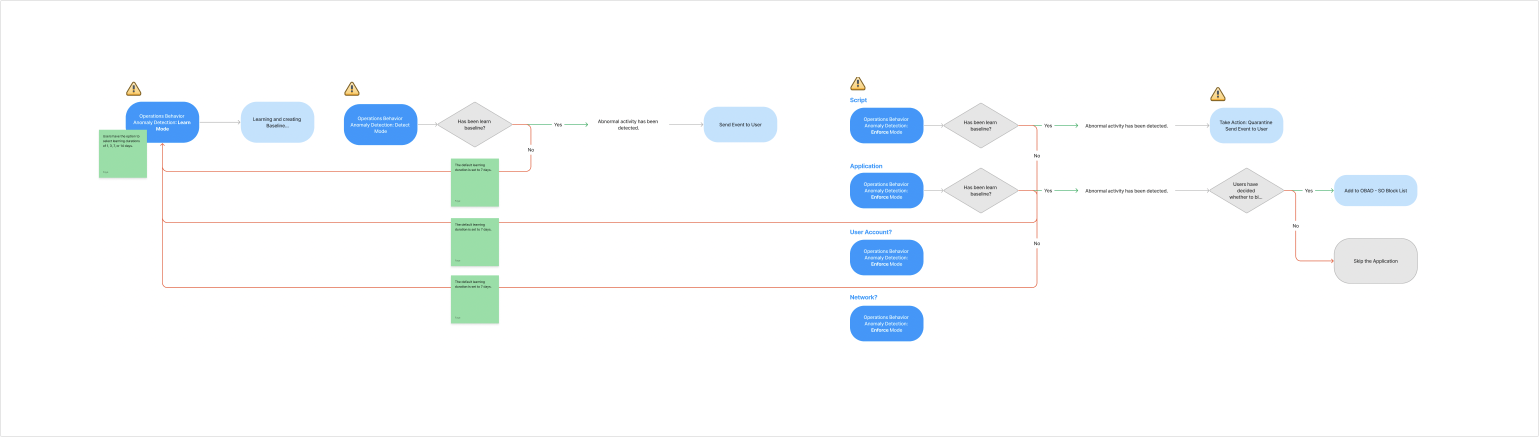
Flow Chart
Design
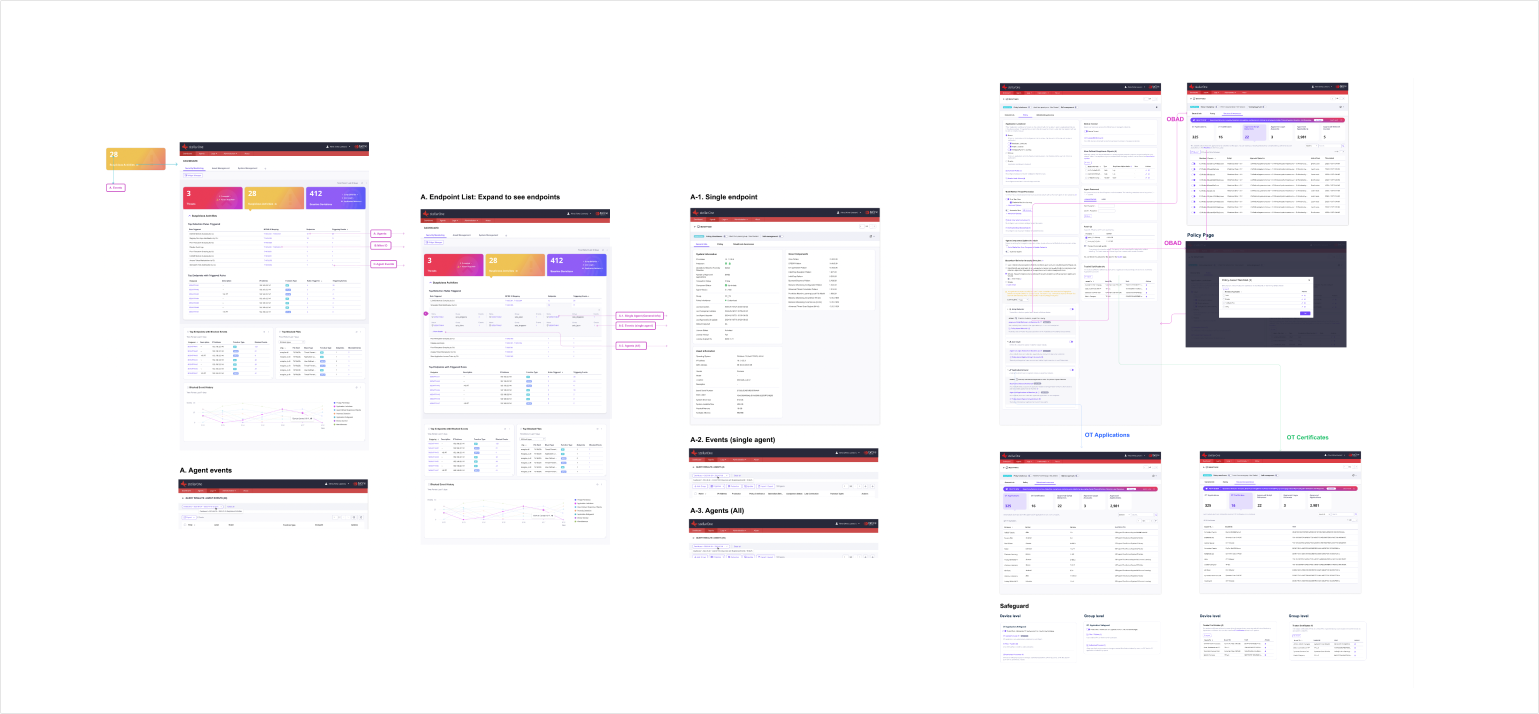
UI Flow
Prototype